Data Privacy
Data secured. Privacy ensured. Your trusted partner in data protection.
Data secured. Privacy ensured. Your trusted partner in data protection.
A data breach of any scale today can cost millions to organizations leading to significant financial losses, related reputational damage and loss of trust.
Upholding the integrity of personal data is a fundamental aspect of data privacy – Organizations from around the world are experiencing unprecedented change in this landscape. Evolving regulations at the national and global levels are forcing businesses to take stock of their operations, practices and technology to address data privacy aspects.
These regulations aim to provide consumers transparency and control over how their data is stored, reinforcing the business obligation to deliver value and build trust.
ECCI understands the risks and challenges companies face in developing economies when it comes to establishing and maintaining effective privacy and data protection programs. We offer an experienced cross-functional team skilled at analyzing, designing and implementing privacy programs for complex establishments.

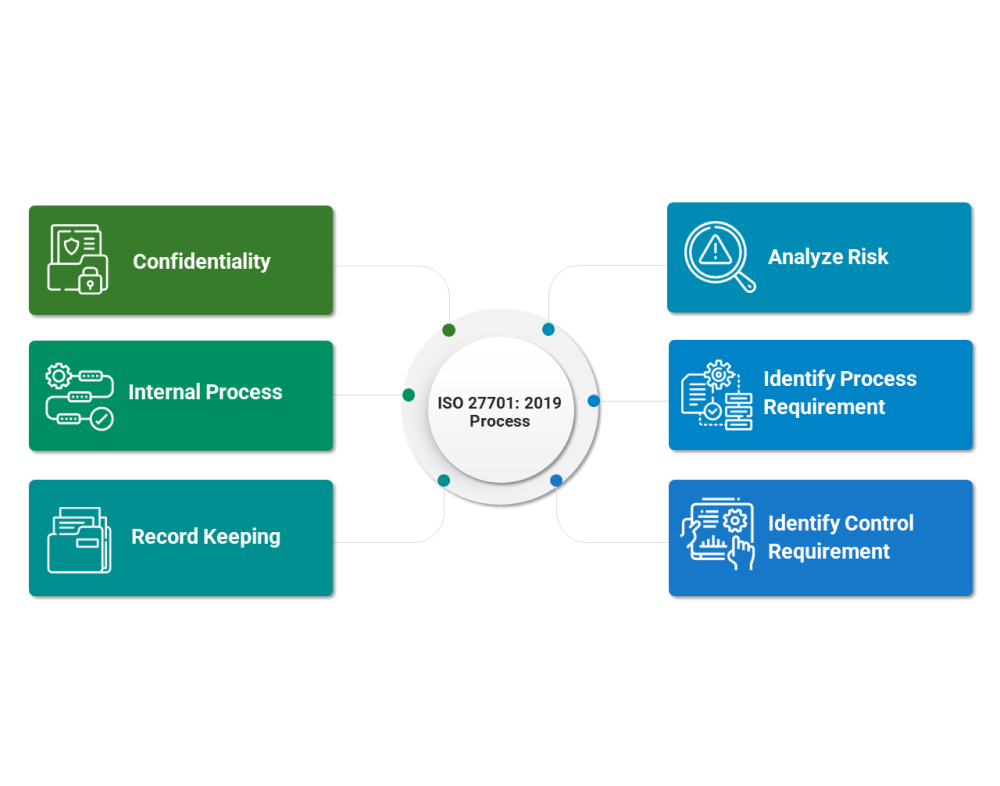
ISO 27701 is an extension of the ISO 27001 framework, incorporating specific privacy controls and considerations to align with regulations such as the GDPR and CCPA. It offers a comprehensive framework for data privacy management, providing guidelines and requirements for establishing, implementing, maintaining, and continually improving a Privacy Information Management System (PIMS).
This framework includes a total of 184 controls categorized into five main groups, specifically tailored to safeguard personal information, and ensure compliance with privacy regulations. These categories
encompass security management, information security
controls, risk management, incident management, and privacy information management.
 (Image Source: https://www.qrcsolutionz.com/apps/home/media/images/iso/ISO%2027701.png)
(Image Source: https://www.qrcsolutionz.com/apps/home/media/images/iso/ISO%2027701.png)The Philippines Data Privacy Act of 2012 (RA 10173) is enacted to protect the fundamental right to privacy and imposes strict requirements on organizations handling personal information.
It is a significant legal framework with 101 sections, providing extensive measures such as protocols for notifying about data breaches and guidelines for cross-border data transfers, the establishment of security measures to ensure the confidentiality, integrity, and availability of sensitive information and obtaining clear and informed consent from individuals before collecting, processing, or disclosing their personal data.
The General Data Protection Regulation (GDPR) constitutes a comprehensive and far-reaching regulatory framework with its 99 articles for data privacy regulation that emphasizes the protection of personal data within the European Union and beyond. Implemented in 2018, it enforces strict guidelines for organizations that handle personal data, ensuring individuals have more control over their information by enforcing accountability upon companies for their management and treatment of sensitive data,
GDPR emphasizes the principles of data minimization, purpose limitation, and transparency, compelling entities to collect only necessary data, specify its intended use, and inform individuals about data processing activities.

Identify and analyze security vulnerabilities and gaps, fortifying defenses based on standards and frameworks.

Evaluate and mitigate potential risks and threats to the organization’s data privacy posture.

Draft required data privacy documentations of various levels addressing different requirements.

Provide recommendations on the data privacy best approach and practices best suited for the organization.

Guide the organization through the process of achieving ISO 27701 certification, ensuring compliance with industry-leading standards and practices.



Ensures adherence to local and global privacy law and regulations, aiding in legal compliance and avoiding hefty penalties.

Well-implemented data privacy framework reduces the risk of unauthorized access or leaks and safeguards sensitive data.

Provides a structured approach to managing privacy risks associated with personally identifiable information (PII).

Having clear protocols in place to ensure quick and effective responses to data breaches or incidents.

Streamlines privacy practices across various regulations, reducing the need for multiple audits and enhancing operational efficiency.

Builds consumer and partner trust by demonstrating commitment to data privacy and security.












COMPANY
WHAT WE DO
CONSULTING SERVICES
RESOURCES
Copyright © 2024. All Rights Reserved.
We use cookies to help us deliver the best experience on our website. By continuing to browse, you agree to our use of cookies. For more details, visit our Privacy Policy.